Сryptodvizh - Бизнес новости
- Когда и как отказываться от предложенной работы Как вежливо отказаться от должности
- Паспортный стол каменск уральский зои космодемьянской
- Открыт завод «Монсанто» в России!
- WMS системы управления складом: плюсы автоматизации Автоматизация системы управления персоналом складского хозяйства
- Высказывания великих и успешных людей о зависти Цитаты о завистливых людях
- Сценарий открытие летних чтений в библиотеке Летние чтения в библиотеках для детей
- Регламент проведения торгов в электронной форме на электронной площадке Южная Электронная Торговая Площадка
- Что собой представляет саморегулируемая организация арбитражных управляющих?
- Как сделать самому электронную цифровую подпись?
- Как разместить план закупок через электронный бюджет Электронный бюджет планирование закупок
- Как подтвердить статус смп и какие преимущества он дает К субъектам регистрации относятся
- Ростелеком — не единственный гос
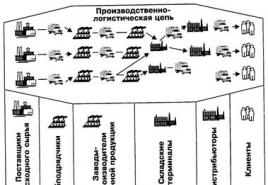
- Эволюция концепции управления цепями поставок
- Назначение swot анализа. SWOT-анализ: что это
- Что это за профессия — таможенное дело
- Как эффективно управлять изменениями в обществе, бизнесе и личной жизни
- Как найти хорошо оплачиваемую работу
- Северный дачник - новости, каталог, консультации
- Информационное письмо о смене генерального директора — образец
- Сведения о государственной регистрации юридических лиц
- Егрип (единый государственный реестр индивидуальных предпринимателей)
- Как получить выписку из егрюл в налоговой по инн или заказать через интернет бесплатно
- Разновидности торгового оборудования
- Отдел снабжения и его роль в производственном процессе предприятия
- Что такое социально ориентированные НКО
- Некоммерческие организации: примеры заботы о людях
- Что такое социально ориентированные НКО
- Как расторгнуть договор или пожаловаться на Ростелеком: последовательность действий и нужные документы
- Публичное (открытое) акционерное общество
- Аудит ит инфраструктуры. Аудит it инфраструктуры. Из чего состоит аудит ИТ-инфраструктуры
- Как полуграмотные крестьяне в XIX веке создали первый российский «сухопутный пароход
- Бланк резюме "Выразительный" с фото
- Список готовых образцов резюме на работу для бесплатного скачивания
- Снижение затрат на предприятии: самые эффективные методы
- Топ профессий, связанных с наукой историей Какие профессии связаны с историей
- Как правильно описать профессиональный опыт работы в резюме Как оформить опыт работы в резюме
- Окончание эры ископаемого топлива предопределено
- Какими могут быть последствия неуплаты коммунальных услуг
- Преимущества для уголовно-исполнительной системы в закупках Преференции уголовно исполнительной системы 44 фз
- Госзаказчик вправе требовать, чтобы автотранспорт обслуживал и ремонтировал только официальный дилер
Похожие статьи